How to Fix the Blue Screen of Death (BSOD)
The Blue Screen of Death (BSOD) is a notorious error screen displayed on Windows computers following a fatal system error. It’s a sight that can cause panic, but understanding what it means and how to fix it can help you resolve the issue and get your system running...
Best Home Wireless Mesh Solutions in 2024
Reliable Wi-Fi coverage is essential for both homes and offices. Traditional routers often struggle to provide consistent coverage, especially in larger spaces or areas with many obstructions. This is where wireless mesh solutions come in, offering robust and seamless...
How to Build Your Business Website: Tips for Success
A strong online presence is essential for any business. Whether you're launching a new venture or revamping your existing site, building a business website is a crucial step in establishing your brand and connecting with customers. Here are some key steps and tips to...
Comprehensive Guide to Securing Your MacBook
As our reliance on digital devices grows, ensuring the security of our laptops becomes increasingly crucial. MacBooks, known for their robust security features, can be further fortified with a few additional steps. This guide outlines essential tips to keep your...
Ultimate Guide to Boosting Your Windows 11 Security
Windows 11 brings a host of new features and a sleek interface, but ensuring your system is secure should always be a top priority. Here’s a comprehensive guide to some lesser-known security tips to keep your Windows 11 machine safe from threats. 1. Enable BitLocker...
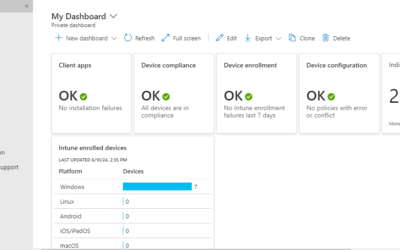
Case Study: Migrating from Google Workspace to Microsoft 365 Business Premium
Overview Company: B2B Consulting Pvt. Ltd.Project: Migration from Google Workspace to Microsoft 365 Business PremiumService Provider: Rational Systems Private LimitedUsers Migrated: 15Key Services Migrated: Email, OneDrive, SharePoint, Endpoint Security via Intune...
Recent Breakthroughs in Quantum Computing: Ushering in a New Era of Computational Power
What is Quantum Computing? Quantum computing is an advanced field of study that leverages the principles of quantum mechanics to perform computations in fundamentally different ways compared to classical computing. Here’s a detailed overview of what quantum computing...
Beating the Heat Wave: A Guide to Network Protection During Summer
India's scorching heat waves pose a significant threat not just to public health but also to our digital infrastructure. Extreme temperatures can fry sensitive electronics and strain power grids, leading to network outages and disruptions. Here's a comprehensive guide...
The Ultimate Guide to Hardware Requirements for Running ChatGPT and other AI Software
The Hardware You Need to Run ChatGPT and Other AI Software With the increasing interest in artificial intelligence (AI) and machine learning (ML), many people are curious about the hardware requirements needed to effectively run advanced AI models like ChatGPT....
Securing Success: The Essential Guide to VPN Solutions for Small Businesses
Welcome to our comprehensive guide on VPN solutions tailored for small businesses. In today's digitally driven world, safeguarding your company's data and ensuring secure remote access are paramount. Virtual Private Networks (VPNs) offer an effective means to achieve...
DIY Tech Support: When to Try It and When to Call a Professional
Encountering technical issues with your devices is almost inevitable. Whether it’s a slow computer, a mysterious error message, or a network connectivity problem, the temptation to fix it yourself can be strong. DIY tech support can be both satisfying and...
How to keep your Computer and Laptop Cool during the Summers.
Summer is a time for beach outings, barbecues, and enjoying the sun. However, the rising temperatures can be a nightmare for your computer or laptop. Overheating can lead to performance issues, hardware damage, and a shorter lifespan for your device. To help you keep...
Unleashing Growth: The Strategic Advantages of Hiring a Virtual Chief Technology Officer (vCTO)
Technology plays a pivotal role in driving success. Whether you're a startup, small business, or...
The Risks of Neglecting Antivirus Subscription Renewal: A Guide to Cybersecurity Consequences
An antivirus software serves as a crucial line of defense against malicious entities seeking to...
Unveiling Industry 4.0: A Revolution in Manufacturing
Industry 4.0: Transforming the Future of Manufacturing In today's fast-paced technological...
Navigating Cybersecurity in 2024: Essential Software and Hardware Investments for Small Businesses
In the fast-paced world of technology, small businesses must stay ahead of the curve to safeguard...
Case Study: Upgrade from Unifi UAP LR to Unifi U6 LR WiFi 6 Wireless Access Point for network better coverage, performance and optimization.
Client Overview: Our one of the existing premium client approached us with a request to enhance...
Case Study: Installation of UniFi 6 Long Range Wireless Access Points in a 4-Storey Factory with Warehouse.
Client Overview A leading furniture manufacturing company embarked on a digital transformation...
Endpoint Security: Safeguarding Your IT Infrastructure in a Dynamic World
Securing your IT infrastructure has never been more critical. With the growing number of cyber...
Top 7 Managed Wireless Access Points for Large Homes, Mansions and Offices
When setting up a managed wireless solution for a large home and office environment, it's crucial...
How the IT Industry Can Lead the Way Towards a Net Zero Future
The global climate crisis demands swift and decisive action from all sectors of society, and the...
Cybersecurity – Cyber Threats Unveiled: Safeguarding Your Digital Fortress
In our increasingly interconnected world, cyber threats have emerged as a formidable adversary,...
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.